RemoteIoT Behind Router: Setup & Raspberry Pi Guide
Is the promise of effortless control over your smart devices from anywhere truly within reach? Remote IoT (Internet of Things) behind a router is not just a technical possibility; it's a game-changer, offering unprecedented flexibility and control in today's interconnected world.
The burgeoning landscape of the Internet of Things (IoT) has brought about a revolution in how we interact with technology. From smart homes to industrial automation, the proliferation of connected devices has created a need for robust, secure, and easily manageable remote access solutions. Whether you're a seasoned professional, a dedicated hobbyist, or simply curious about the potential of connected devices, understanding the principles of remote IoT behind a router is essential. This article dives deep into the world of Remote IoT setups, focusing on practical examples and actionable advice to help you harness the full potential of this technology.
In this guide, we will explore the intricate details of setting up and managing remote access to IoT devices, even when they are situated behind a router. We will examine the essential components, from the core concept of remote IoT to the practical implementation using a Raspberry Pi.
In the dynamic field of the Internet of Things, the Raspberry Pi stands out as a versatile and affordable solution, acting as a cornerstone for many IoT projects. Its affordability and the vast range of software available make it a top pick for IoT developers of all levels. Remote IoT configurations, especially those employing Raspberry Pi, have become increasingly sought after, and the ability to manage these devices remotely can significantly improve any IoT project.
This guide will help you understand how to set up remote SSH access for IoT devices, secure and efficient communication even when they are behind a router, all while ensuring the highest standards of security and data integrity. This is not just about connecting devices; it's about crafting a secure pathway for seamless communication in our modern world.
As more businesses and households embrace the IoT, understanding how to set up and manage remote IoT devices behind a router has become absolutely crucial. The ability to control and monitor devices remotely is no longer a luxury but a necessity, providing convenience, efficiency, and peace of mind. Let's explore the best practices for securing connections, the foundational principles, and the key reasons behind the adoption of remote IoT. Consider this your blueprint to master remote device management.
The essence of remote IoT behind a router lies in its ability to establish seamless communication between devices that are not on the same local network. This is often achieved by leveraging specific technologies and configurations that enable devices to securely connect to and interact with each other, irrespective of their physical location.
As the digital landscape continues to evolve, the importance of secure remote access to IoT devices grows exponentially. Whether managing a home automation system or industrial IoT solutions, securing access to devices behind a router is paramount. The need for robust security protocols cannot be overstated, as it protects sensitive data and prevents unauthorized access. This also ensures the reliability of all IoT systems.
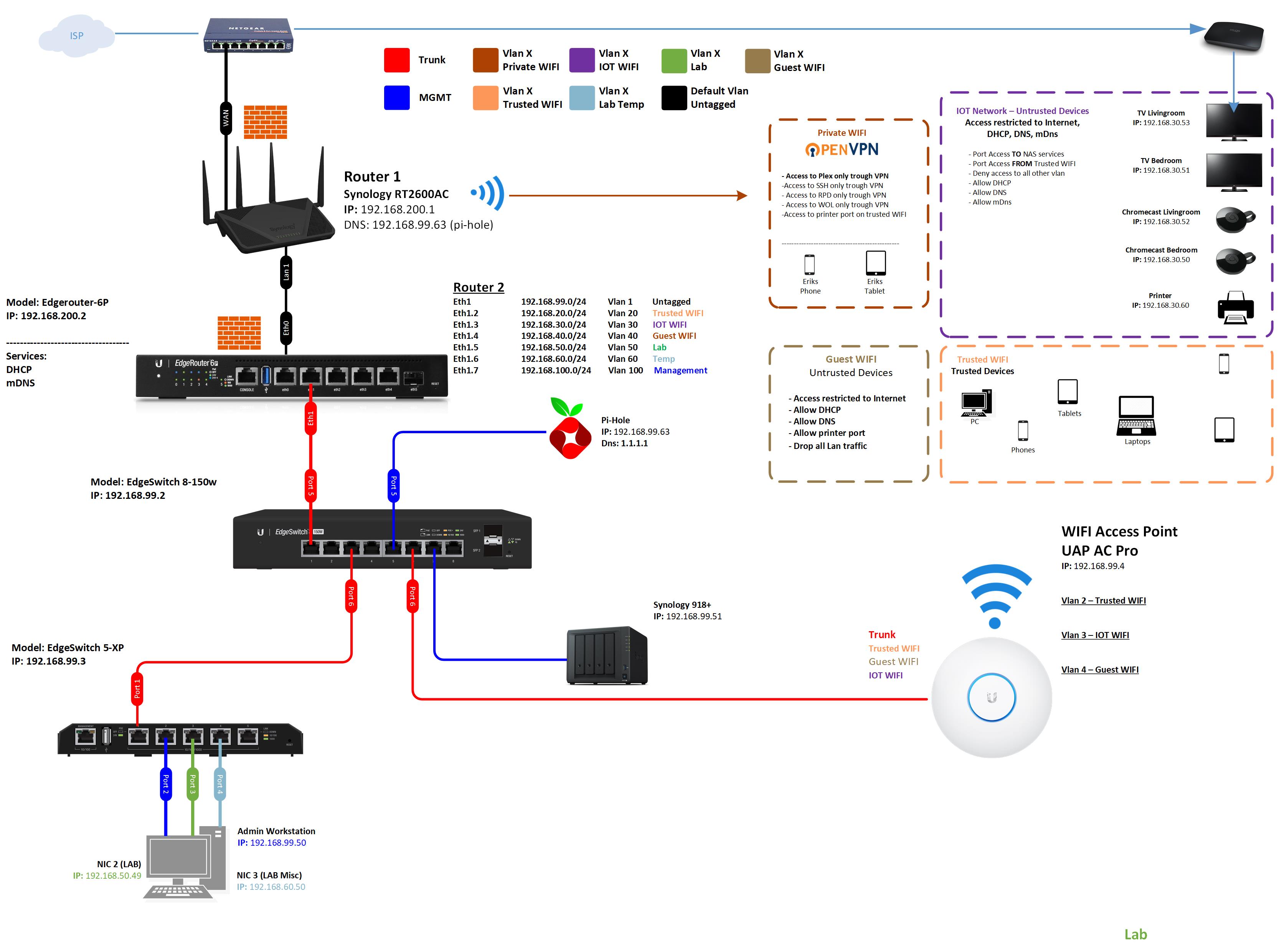
The core of remote IoT setups involves several key elements, including the router itself, which acts as a gateway, and the devices that you want to access remotely. Devices like Raspberry Pi are frequently used to create a centralized control hub.
Understanding the Router's Role:The router plays a critical role in facilitating remote access. It acts as the gatekeeper of your local network, forwarding data from the internet to your connected devices and vice versa. Configuring the router properly is essential for ensuring that remote access works seamlessly.
The Significance of Port Forwarding:Port forwarding is a technique that directs incoming network traffic from a specific port on your router to a specific device within your local network. This is one of the primary methods to ensure you have the best in remote device management. This allows you to reach your devices from any location with an internet connection. You'll need to understand the technical specifics to get the best experience from it.
Essential Security Practices:Securing your connections is paramount when setting up remote access. This includes using strong passwords, keeping your software updated, and enabling encryption. Implementing these practices protects your devices from potential threats and ensures the integrity of your data.
One of the popular solutions for remote IoT management is the Raspberry Pi, a compact and affordable computing device. Known for its versatility, the Raspberry Pi can be easily integrated into IoT projects. It is able to act as a gateway for other devices, providing a secure and controllable point of access. Setting up remote access with a Raspberry Pi involves several steps.
Setting Up the Raspberry Pi:Begin by installing the operating system of your choice on the Raspberry Pi (e.g., Raspberry Pi OS). Configure the network settings to ensure it can connect to your local network. Enable SSH (Secure Shell) access, which allows you to securely access the Pi from another device.
Configuring the Router:Access your router's web interface and navigate to the port forwarding settings. Create a rule that forwards traffic from a specific external port on your router to the Raspberry Pi's internal IP address and the port that SSH is running on (typically port 22). This configuration is a key aspect for enabling remote access.
Accessing the Raspberry Pi Remotely:Once you have set up the router and the Raspberry Pi, you can access your Raspberry Pi remotely by using its external IP address and the external port you configured in the router settings. You'll be able to securely access your Raspberry Pi. Using the correct settings is paramount.
Best Practices for Secure Connections:When setting up remote access, security should be your top priority. Use strong passwords, enable two-factor authentication, and keep your software up-to-date. Consider using a VPN (Virtual Private Network) for an additional layer of security, encrypting the communication between your devices and providing a secure environment. These measures are critical for safeguarding your devices and your data.
Beyond basic SSH access, remote IoT offers a wide range of possibilities. You can set up remote desktop connections, allowing you to view and control the graphical user interface of your Raspberry Pi from anywhere. You can also configure a web server on your Raspberry Pi and remotely access web applications hosted on the device. Advanced users can explore setting up secure tunnels to create a completely encrypted connection between devices. These options offer flexibility and the ability to tailor remote access to the specific requirements of each project.
Remote Desktop:Enabling remote desktop access allows you to control the graphical user interface of your Raspberry Pi from anywhere. This is useful for tasks that require a visual interface. You can use tools such as VNC (Virtual Network Computing) or RDP (Remote Desktop Protocol) to accomplish this. This enables you to troubleshoot, administer, and use applications installed on your Pi.
Web Servers:By setting up a web server on your Raspberry Pi, you can host web applications and access them remotely via a web browser. This opens up possibilities for monitoring and controlling your IoT devices through a web interface. You can use web technologies to create custom dashboards and user interfaces.
Secure Tunnels:Creating secure tunnels, often using SSH tunnels, adds an extra layer of security. This encrypts all traffic between your devices, protecting data from interception. It is a useful method for sensitive data and applications.
Introduction to Remote IoT: Why Use Remote IoT?
The adoption of remote IoT solutions is driven by several key advantages. First, remote access provides the convenience of controlling and monitoring your devices from anywhere, at any time. This is especially valuable for home automation, allowing you to adjust settings, view camera feeds, or manage appliances even when you're away from home.
Second, remote access can significantly improve the efficiency of your IoT projects. You can troubleshoot and debug issues remotely, eliminating the need for physical presence. This is particularly useful for industrial IoT applications where remote maintenance can save time and reduce downtime.
Finally, remote IoT enhances security. By securely accessing your devices remotely, you can monitor and respond to security threats promptly, protecting your property and your data. Many companies are also using remote IoT to improve efficiency in their businesses.
Real-World Examples:
Smart Home Automation:Imagine being able to control your home's lighting, heating, and security systems from your phone, no matter where you are. This is the power of remote IoT in action. Remote access lets you customize your home environment, enhance your living experience, and increase energy efficiency. You can integrate various IoT devices into a centralized control system for ease of use.
Industrial IoT Solutions:In industrial settings, remote IoT is essential for monitoring and controlling machinery and equipment. From remote diagnostics to real-time data monitoring, remote access enables proactive maintenance, minimizes downtime, and ensures optimal performance. This is also essential to track assets and the status of various equipment.
Remote Monitoring and Control:Remote IoT also opens the door to the remote management of devices. Remote access can include the management of sensors, data loggers, and other equipment that may be in remote locations. These configurations can include environmental monitoring, weather stations, and other instruments located in areas with limited physical access.
Troubleshooting and Maintenance:Remote access simplifies the processes of diagnosing and fixing issues. This cuts down on the need for onsite support. Remote access makes it easier to troubleshoot any issue.
Challenges and Solutions:Setting up and managing remote IoT systems can present several challenges. Common issues include network configuration, security vulnerabilities, and bandwidth limitations. By understanding these challenges and implementing effective solutions, you can ensure the smooth operation of your remote IoT projects.
Network Configuration:Network configuration can be complex. You need to understand port forwarding, firewall rules, and IP addressing. Incorrectly configured settings will render your remote access useless. Carefully planning your setup will help you resolve any issues that you encounter.
Security Vulnerabilities:Security is a critical concern. Weak passwords, outdated software, and unencrypted communication are potential threats that malicious actors can exploit. Always prioritize security when setting up remote access to minimize risks.
Bandwidth Limitations:Bandwidth limitations can impact the performance of remote access, especially for applications that require significant data transfer, such as streaming video. Optimizing your network settings and using efficient data transmission protocols can help mitigate this issue.
Remote IoT Behind Router: Practical Implementation
In this practical example, we'll focus on connecting a Raspberry Pi to a router via Ethernet. This configuration illustrates a common use case for remote IoT. We will guide you through the fundamental steps to set up remote SSH access for your Raspberry Pi, enabling you to securely manage it from anywhere in the world.
Hardware and Software Requirements:First, you'll need a Raspberry Pi and an Ethernet cable. A stable internet connection is essential for both the Raspberry Pi and the device you will use to access it remotely. A computer (laptop or desktop) is required for configuring the router and accessing the Raspberry Pi. Make sure the Raspberry Pi OS or your desired operating system is installed on a microSD card.
Step-by-Step Guide:1. Setting Up the Raspberry Pi:Insert the microSD card with the Raspberry Pi OS into the Raspberry Pi. Connect the Raspberry Pi to your router via Ethernet. Power on the Raspberry Pi.
2. Configuring the Router:Log in to your router's web interface. Locate the port forwarding settings. Create a port forwarding rule that maps an external port on your router (e.g., 2222) to the Raspberry Pi's internal IP address on port 22 (SSH). You may also need to set a static IP address for your Raspberry Pi in the router settings to ensure the IP address does not change.
3. Accessing Remotely:From a device with an internet connection, open an SSH client (e.g., PuTTY, Terminal). Enter your router's external IP address, the external port you specified in the port forwarding rule, and the username and password for your Raspberry Pi. You should be able to securely access your Raspberry Pi.
4. Security Considerations:Change the default password for your Raspberry Pi. Consider using key-based authentication instead of passwords. Regularly update your Raspberry Pi's software to address security vulnerabilities. This will help you to ensure the security of all devices.
Advanced Tips and Techniques:For more advanced scenarios, consider setting up a dynamic DNS service. This service updates your IP address automatically, making it easier to access your Raspberry Pi if your internet service provider assigns you a dynamic IP address. Explore creating a VPN server on your Raspberry Pi to establish a secure connection to your home network. These advanced configurations offer additional control over your projects.
Setting up Dynamic DNS:Dynamic DNS services allow you to access your home network even if your public IP address changes. These services automatically update a domain name, allowing you to use a memorable address to access your Raspberry Pi. Many routers support dynamic DNS directly.
Creating a VPN server:A VPN provides a secure, encrypted connection to your home network. By setting up a VPN server on your Raspberry Pi, you can ensure all traffic between your device and your home network is protected. OpenVPN is a popular VPN server software.
Troubleshooting Common Issues:If you encounter problems, start by checking the basics. Ensure that your Raspberry Pi is connected to the internet, the router settings are correct, and that you are using the right credentials. Use port scanning tools to verify that the ports you configured are open. If all else fails, consult online resources and forums. Finding support can also help you to troubleshoot any issues.
Checking your internet connection:Verify that both your Raspberry Pi and the remote device have active internet connections. Problems with these connections can lead to issues with remote access.
Router settings:Double-check the port forwarding rules, firewall settings, and any other relevant configurations on your router. The router configuration has to be correct for remote access to work.
Credentials:Make sure you have the correct username and password for your Raspberry Pi.
Resources and Further Reading:The world of remote IoT is vast and continuously evolving. There is a wealth of information available. Explore online tutorials, documentation, and community forums to expand your knowledge. Engage with online communities. Don't hesitate to experiment with different setups. Remember to prioritize security at all times.
Online Tutorials and Documentation:There is a rich array of online resources available for learning about remote IoT, including articles, videos, and tutorials.
Community Forums:Engage with online communities, ask questions, and learn from the experiences of other users. Sharing your knowledge and expertise will also help you stay up to date.
Conclusion:Remote IoT is a powerful solution for managing connected devices. By understanding the principles of remote IoT, you can create secure, flexible solutions for various applications. Whether for home automation or industrial automation, the ability to access and manage devices remotely enhances both convenience and efficiency. Always prioritize security to protect your devices and data. Stay current with the latest developments to stay ahead of any threats.