SSH To IoT Devices On AWS: Secure Remote Access Guide
In an era defined by interconnected devices, can you securely access and manage your IoT devices, regardless of their location or network restrictions? The answer lies in mastering IoT SSH access via AWS, unlocking a new frontier of remote device management.
The modern landscape of the Internet of Things (IoT) presents a myriad of challenges, particularly in the realm of secure access and device management. Firewalls, while essential for safeguarding IoT devices, often erect barriers that impede remote access and control. Troubleshooting, configuration updates, and other operational tasks become cumbersome, often necessitating on-site visits from technicians. This not only increases the complexity of device management but also significantly inflates associated costs.
Fortunately, Amazon Web Services (AWS) provides a robust platform to address these challenges. By leveraging the power of AWS, organizations can establish secure and efficient connections to their IoT devices, regardless of their physical location or network configurations. This is achieved through a combination of secure tunneling, SSH (Secure Shell) protocols, and the AWS IoT platform, creating a robust solution for remote access and management. This article will explore the key aspects of this innovative approach, offering insights into best practices, practical implementation strategies, and the overall benefits of harnessing AWS for IoT device management.
Before we dive deeper, let's consider the core problem. Accessing and managing IoT devices that reside behind firewalls, particularly those blocking inbound traffic, is notoriously difficult. The traditional methods of on-site visits are expensive and time-consuming, making efficient device management a significant hurdle. AWS offers a powerful alternative: secure tunneling.
Secure tunneling, a feature of AWS IoT Device Management, enables bidirectional communication with remote devices over a secure connection managed by AWS IoT. This eliminates the need to modify existing firewall rules, maintaining the same level of security while enabling remote access. With secure tunneling, the complications of managing devices across geographically diverse areas become manageable.
The process of establishing a secure SSH connection with an IoT device on AWS might seem daunting at first glance, but with the right knowledge and tools, it is entirely achievable. By following the comprehensive guidance and strategies we will outline, you can establish a secure and efficient connection that perfectly aligns with your needs.
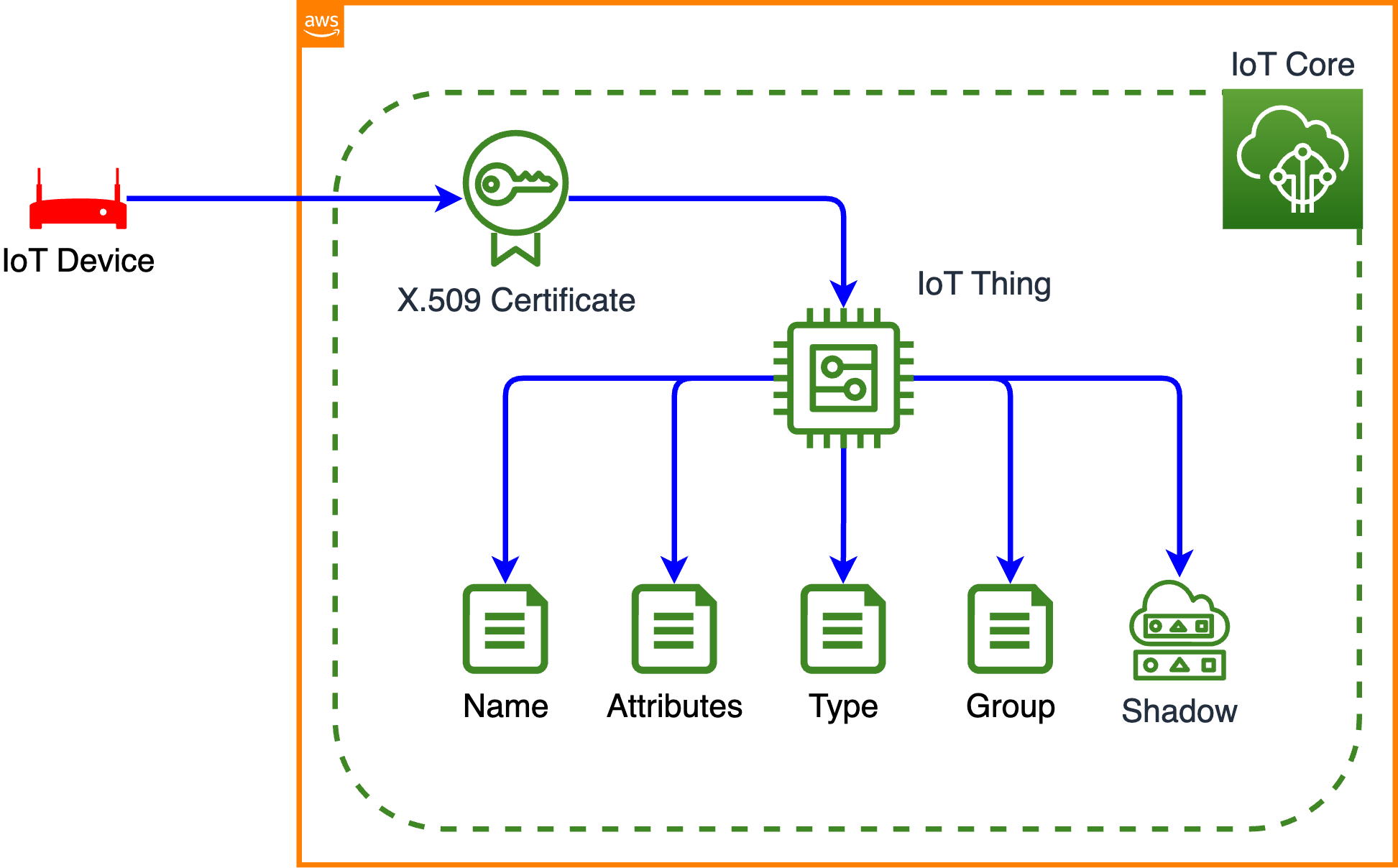
The cornerstone of this approach is the IoT device agent, a software component that runs on the remote IoT device. This agent securely connects to the AWS IoT Device Gateway, utilizing an MQTT topic subscription to receive commands and relay information. For detailed information on connecting a device to the AWS IoT Device Gateway, AWS provides comprehensive documentation.
As the number of organizations embracing cloud computing and IoT continues to surge, identifying the best remote SSH IoT device access solutions on AWS becomes more and more critical. This is not just a convenience; it's a necessity for effective management, ensuring your devices are running smoothly, and addressing any issues that arise. With AWS as the framework, you have the building blocks for a secure and reliable IoT remote access setup, ensuring the longevity and efficacy of your IoT projects.
The path to seamless integration with AWS involves several key steps: setting up your environment, configuring the IoT devices to connect to an EC2 instance via SSH, and verifying the SSH connection. By following these procedures, you will build a system that is robust and easy to use, allowing you to manage devices remotely with confidence.
Let's clarify the concept: SSH, or Secure Shell, functions as a digital superhero cape for your device connections. It employs encryption to secure your data, preventing unauthorized access and ensuring that your IoT devices remain safe while interacting with AWS services. It allows developers, technicians, and tech enthusiasts to troubleshoot issues and deploy updates to devices remotely, regardless of location.
The advantages of leveraging AWS for IoT SSH access are significant. AWS is the ultimate toolkit for managing SSH IoT device access, with powerful services that simplify the process of securing and scaling remote access for your IoT devices. AWS enables you to build resilient, scalable, and secure remote device management solutions that are ready for the demands of the future.
To get the most out of your IoT remote access setup on AWS, you should optimize your SSH configuration. This includes setting up the secure connections, configuring the devices and making sure that your access is not just accessible, but also secure, resilient, and aligned to your specific business needs.
In the AWS IoT console, creating a tunnel can be achieved from the "Tunnels" hub page or the details page of a created "Thing".
Beyond the practical applications, the implications of this technology are far-reaching. SSH plays a pivotal role in the IoT ecosystem, allowing users to securely manage devices, troubleshoot issues, and deploy updates. By addressing these issues promptly, you can maintain uninterrupted access to your IoT devices.
Best Practices for IoT SSH Configuration on AWS
To guarantee a seamless and secure experience when remotely connecting to IoT devices using SSH, follow these best practices:
- Comprehensive Documentation: Keep detailed records of your device settings and AWS configurations for easy reference. This includes IP addresses, security group rules, and any custom configurations.
- Strong Authentication: Utilize strong authentication methods, such as key-based authentication rather than password-based authentication, to enhance security.
- Regular Security Audits: Conduct regular security audits of your SSH configurations and access controls to identify and mitigate potential vulnerabilities.
- Least Privilege Principle: Grant only the necessary permissions to users and devices to minimize the potential impact of a security breach.
- Monitor and Log: Implement monitoring and logging to track SSH access attempts and identify suspicious activity.
- Keep Software Updated: Always maintain up-to-date software on your IoT devices and EC2 instances to address known vulnerabilities.
Addressing Potential Challenges
While the benefits of IoT SSH access on AWS are considerable, some potential challenges may arise:
- Firewall Configuration: Ensuring correct firewall rules on both the IoT device side and the AWS side is crucial.
- Network Connectivity: Maintaining reliable network connectivity between the IoT devices, the AWS IoT Device Gateway, and your EC2 instance is essential.
- Security Best Practices: Strict adherence to security best practices is paramount to avoid unauthorized access and protect your devices.
- Key Management: Secure key management is necessary to manage SSH key pairs safely to avoid unauthorized access to devices.
- Troubleshooting: Have strategies in place for troubleshooting common issues like connectivity problems and authentication errors.
Tools and Technologies: The Building Blocks of Secure Access
Implementing SSH for IoT device access on AWS requires a variety of tools and technologies to facilitate secure and reliable connections. A brief overview of some of the key components includes:
- AWS IoT Device Gateway: The central component in the AWS IoT ecosystem that enables secure and reliable communication between the IoT devices and the AWS cloud.
- AWS IoT Device Agent: Software that runs on your IoT devices and connects to the AWS IoT Device Gateway. This agent handles communication, MQTT subscriptions, and other tasks.
- AWS IoT Secure Tunneling: Provides secure, bi-directional communication with remote devices over a secure connection managed by AWS IoT, eliminating the need to change firewall rules.
- SSH Client (e.g., OpenSSH, PuTTY): Clients that provide the interface to interact with the remote device via SSH. These tools allow you to establish a secure connection and execute commands.
- SSH Server (e.g., OpenSSH Server): The server-side component that runs on your IoT devices or the EC2 instance, handling incoming SSH connections.
- EC2 Instances: Virtual servers on AWS that can act as a "jump box" for managing and accessing your IoT devices. They enable you to consolidate access and enhance security.
- MQTT (Message Queuing Telemetry Transport): A lightweight messaging protocol used for communication between devices and the AWS IoT Device Gateway. It supports bidirectional communication using topics and subscriptions.
- Firewall: Important for protecting IoT devices.
A Step-by-Step Guide to IoT SSH Access on AWS
Here's a detailed walkthrough of the process:
- Prerequisites:
- An AWS account with the necessary permissions (IAM).
- Familiarity with the AWS Management Console.
- An existing IoT device or a device you're planning to integrate.
- An understanding of basic networking concepts.
- Device Setup
- Install the IoT Device Agent: Install and configure the AWS IoT Device Agent on your IoT device. This agent enables the device to securely communicate with the AWS IoT Device Gateway and establishes an MQTT topic subscription.
- Configure an MQTT Topic Subscription: Configure your device to subscribe to an MQTT topic. This subscription allows the device to receive commands, configurations, and updates.
- EC2 Instance Setup:
- Launch an EC2 Instance: Launch an Amazon EC2 instance within your AWS environment. This instance will serve as your SSH server. Choose an appropriate instance type based on your needs (consider the resources you will need and the expected volume of SSH traffic).
- Security Group Configuration: Create or modify a security group to allow SSH traffic (port 22) from your IP address or a trusted network. Ensure that the security group is configured to permit inbound traffic on port 22 from the authorized sources.
- Secure Tunneling Configuration:
- Create an AWS IoT Thing: In the AWS IoT console, create a "thing" that represents your IoT device.
- Create a Secure Tunnel: Navigate to the "Tunnels" section in the AWS IoT console, and create a secure tunnel. This will establish a secure connection to your IoT device. This connection will facilitate bi-directional communication to your device via a secure channel managed by AWS.
- Configure the Tunnel: The tunnel can be configured either via the AWS Management Console or using the AWS IoT API.
- SSH Key Pair Management:
- Generate an SSH Key Pair (if not already done): Use a tool like `ssh-keygen` to generate a key pair on your local machine or an instance within your AWS environment.
- Upload the Public Key: Upload the public key to the authorized_keys file on the EC2 instance.
- Connecting to the EC2 Instance via SSH:
- Connect to the EC2 Instance: Using an SSH client (like OpenSSH, PuTTY, or similar), connect to your EC2 instance via its public IP address or DNS name.
- Establishing the SSH Connection to the IoT Device:
- Configure Port Forwarding: On your EC2 instance, configure port forwarding to forward SSH traffic from a local port on the EC2 instance to the appropriate port of your IoT device.
- Connect to the IoT Device through the Tunnel: Establish an SSH connection to the IoT device by connecting to the local port on the EC2 instance.
- Verification:
- Test the SSH Connection: Successfully log in to the IoT device via SSH.
- Troubleshooting: Resolve any connection issues. If you are having trouble connecting, double-check the following:
- Confirm that the EC2 security group allows SSH traffic.
- Verify that the tunnel is active.
- Make sure the correct ports are forwarded.
Practical Considerations
Let's move to the practical considerations for implementing this setup, which include how to connect an SSH IoT device on AWS using Windows. It's achievable by adhering to key steps that facilitate secure and efficient access:
- Choose an SSH Client: Many options exist, including PuTTY, Windows Terminal, and others. Select a client you're comfortable with.
- Key Pair Management (Recommended): Create an SSH key pair (private/public) using a tool like PuTTYgen to enhance security.
- EC2 Instance Configuration (as mentioned previously): Launch an EC2 instance (consider using an Amazon Linux AMI).
- Security Group: Create a security group that allows SSH traffic on port 22 from your IP address.
- Accessing via the EC2 Instance: Use your SSH client (PuTTY, etc.) to connect to the EC2 instance.
- Using AWS IoT Secure Tunneling: Set up a secure tunnel using the AWS IoT console.
- Connecting to Your Device: Use port forwarding and the tunnel information provided by the AWS IoT console to access your IoT device.
Expanding on Security
The cornerstone of secure IoT device access on AWS is robust security measures. For secure SSH access to your IoT devices, here's a summary of best practices:
- Strong Authentication: Implement SSH key-based authentication instead of passwords. This enhances security by using cryptographic keys instead of easily guessable passwords.
- Regular Updates: Frequently update your operating systems, SSH software, and other associated tools. This protects against known vulnerabilities.
- Firewall Configuration: Properly configure firewalls, not only on your IoT devices but also on the EC2 instance and in the AWS security groups.
- Access Control Lists (ACLs): Use ACLs to control network traffic and further limit exposure.
- Principle of Least Privilege: Grant only the minimum necessary permissions to each user or device.
- Monitoring and Logging: Implement robust logging and monitoring systems to track access attempts and network activity, identifying and responding to potential security breaches in real-time.
Alternative Approaches and Advanced Strategies
Here are a few additional strategies:
- Using a Bastion Host (Jump Box): In more complex scenarios, a bastion host can be used to consolidate SSH access, making it more manageable and secure.
- Automating the Setup: Utilize automation tools (e.g., AWS CloudFormation, Terraform) to streamline the deployment of your infrastructure, ensuring consistency and ease of scaling.
- Leveraging IAM Roles: Use IAM roles to give the EC2 instance and/or your users the required permissions to access AWS IoT and other services securely.
- Implementing Two-Factor Authentication (2FA): For added security, implement 2FA on your SSH access, ensuring only authorized users can access the devices.
- Integrating with Centralized Authentication Systems: Integrate your SSH access with a centralized authentication system (e.g., LDAP, Active Directory) for streamlined user management.
Conclusion: A Path Forward for Secure IoT Device Management
In conclusion, SSH and AWS are essential tools in the management of modern IoT devices, offering powerful solutions to the security challenges that arise. By understanding the fundamental concepts, embracing the recommended best practices, and leveraging AWS services, organizations can establish a secure, efficient, and scalable approach to remote IoT device management. As technology continues to evolve, remaining informed and adaptable will be key to optimizing the future of IoT device management, securing the connected devices of tomorrow. As we progress, it is critical to continue learning about the emerging best practices, and AWS's evolving tools for the optimal security of IoT devices.