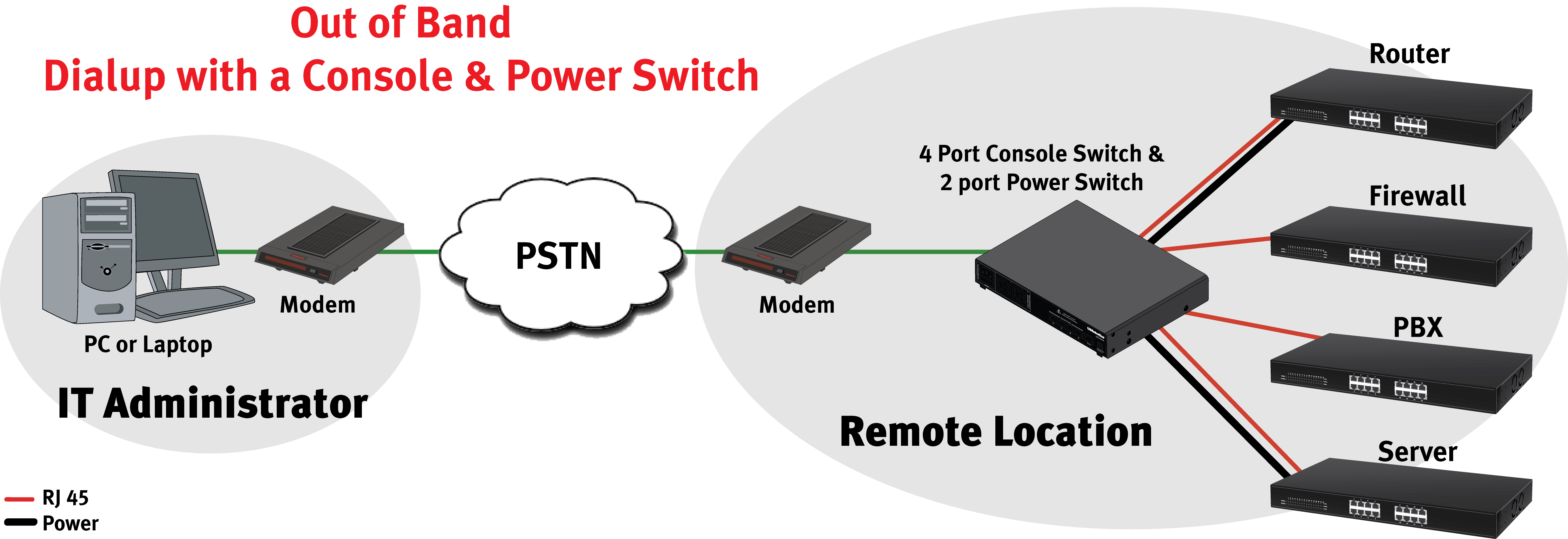
Remote Access Behind A Router: Your Ultimate Guide
Can you effortlessly connect to devices nestled behind your home or office router, no matter where you are? The answer, surprisingly, lies in understanding the nuances of "remote access" a capability that unlocks unparalleled control and flexibility over your digital world.
The initial step in this process often involves establishing remote access to the cellular router itself. This might include enabling remote SSH access, if supported. However, the journey to achieving this can present several hurdles, particularly when dealing with Network Address Translation (NAT) and the intricacies of multiple routers.
Consider a scenario: you have a network behind a router, and behind that NAT, a client. You only possess access to the first router (let's call it 'a'), while the second router (labelled 'b'), and the NAT router, remain out of reach. The challenge then becomes: how do you establish a direct connection to 'b' from 'a', especially when port forwarding and UPnP are off the table? The core principle revolves around finding a workaround, a clever trick that circumvents these limitations.
It's crucial to remember that setting up remote access requires careful planning and execution, emphasizing both optimal performance and security. Identifying your router's IP address is the first practical step; often, this information is indicated in the format 192.168.1.1 or 192.168.0.1, though this will vary depending on your location.
One method involves utilizing a reverse proxy, accessible within your local network. You connect to the server from a device in your local network, preferably a reverse proxy. Subsequently, you set your domain or subdomains to point to your VPS IP address. The VPS then forwards all traffic through the VPN to your local device. Ultimately, the local device (the reverse proxy) manages the traffic on your local network.
Consider an example: you're working on an IoT project and have a device connected to a cellular router, such as a Smartflex. This device, connected to eth0, has a private address (e.g., 192.168.1.5). The objective is to remotely access the device's web GUI via laptop or cellphone. The question then becomes: Can this be achieved using NAT?
Here's a simplified solution. Assuming your programmable device functions on port 22 with an IP of 192.168.1.5, and your public IP is 122.176.11.55, you can configure your router to forward a WAN port (e.g., 8022) to 192.168.1.5:22. Now, you can access the device remotely from anywhere on the internet by accessing 122.176.11.55:8022 instead of 192.168.1.5:22 in your IDE.
This method involves a comprehensive understanding of networking fundamentals. However, remember that achieving secure and efficient remote access requires careful consideration of multiple factors, including protocol selection and the implementation of robust security measures. The goal is to build a system that is not only functional but also secure against potential threats.
Take the case of a user who has a router with DynDNS set up, can VPN to their desktop via Hamachi, can use RDP via Windows 7 RDP, and generally performs "fancy tricks." The remaining challenge is to browse a networked device behind the router from their laptop over the internet. To enable connections to devices and services behind the remote router, one of several methods must be employed, including those previously mentioned.
For remote access, you can choose from the range of 0 to 255, avoiding the value 89, which is the default dedicated for VPN accesses. Your programmable device works on port 22 and has the ip 192.168.1.5. Your public IP is 122.176.11.55. Then you can go into your router's setting and forward a wan port (for eg, 8022) to 192.168.1.5:22. Now, you can remotely access the device from anywhere through the internet by accessing 122.176.11.55:8022 instead of 192.168.1.5:22 in your ide.
Another common scenario is when a household uses a router that is also used by multiple people, so the user may want to connect a second router via ethernet, install a VPN on it, and then connect their devices to the second router and an unmanaged switch. This setup is perfect for managing devices like PoE cameras, PoE lights, and temperature and humidity sensors.
For those leveraging the Emnify openVPN service, the static IP address assigned to your router, visible within a red box, can be used to access and troubleshoot the device itself.
To implement remote access effectively, you need an account to add the router to the remote management system. The process of adding your router to a service like Teltonika RMS requires an RMS account.
The intricacies of establishing connections between two devices on separate private RFC1918 networks, both behind NAT, without direct access to each other, highlights a complex networking challenge. A workaround might involve setting the router to bypass a specific IP address from the hotspot and creating an entry for the specific IP address, with the type set as "bypassed." Ensuring the device has a static IP address on the WAN port and is listening on a specific port with remote access enabled is also vital.
Using a VPN allows you to access your IoT device from any location globally, as long as you have an internet connection. Whether you're overseas or on the move, you can control and monitor your device as if you were physically present.
The concept of remote access is not just limited to specific technologies or applications; it's a fundamental principle. For example, selecting "internet and home network" can be an effective solution for remote access configuration. Successfully enabling an OpenVPN server on a router and connecting to it from a remote OpenVPN client, which has been assigned an IP address like 10.8.0.6, demonstrates the utility and flexibility of these systems.
However, managing a Raspberry Pi behind a firewall or a NAT router without a public IP address can be a significant challenge for remote control and maintenance. Changing the VPN/firewall configuration can be cumbersome if the Raspberry Pi is behind a corporate firewall that does not allow SSH or VNC connections. In cases where your modem is also a router and your devices are in separate networks, reconfiguring your Wi-Fi router as an access point can be more efficient, ensuring all your devices are within a single IP range.
For instance, the IXRouter connects to a VPN server within the Ixon cloud infrastructure. It automatically seeks the appropriate service and the fastest available server. This provides worldwide remote access to devices behind the router, such as PLCs and devices in a local machine network.
The remote access function is often located within the advanced settings of your router. In Netgear routers, it is found under Settings > Remote Management. In D-Link routers, it is usually located under Tools > Administration > Enable Remote Management. Similarly, in Linksys routers, you can find it under Administration > Remote Management.
Configuring remote access SSL VPN on a Sophos firewall when it is behind a NAT device is another advanced scenario. To achieve this, you typically need configuration access to the NAT device/router, or you might need to request your ISP to make the necessary changes.
The term "remote access device behind router" refers to the capability to connect to devices within a local network from an external location. As telecommuting grows and people manage their devices remotely, understanding how remote access works behind a router is critical for maintaining security and ensuring seamless connectivity.