Deepfake & Deep Hot Link Websites: Explore & Understand Now
Is the digital world truly offering us a new frontier of creative expression, or are we hurtling toward a landscape fraught with deception? The emergence of deepfakes and deep hot links, interwoven with sophisticated link management, is fundamentally reshaping how we consume information and interact online, for better or worse.
The echoes of this digital transformation reverberate across multiple platforms, from the visually stunning realm of photography to the often-murky depths of online content. We are witnessing a technological revolution, driven by artificial intelligence and advanced algorithms, that is blurring the lines between reality and simulation. It's a complex tapestry, woven with threads of innovation, ethical considerations, and the ever-present question of how we, as users, will navigate this evolving digital terrain.
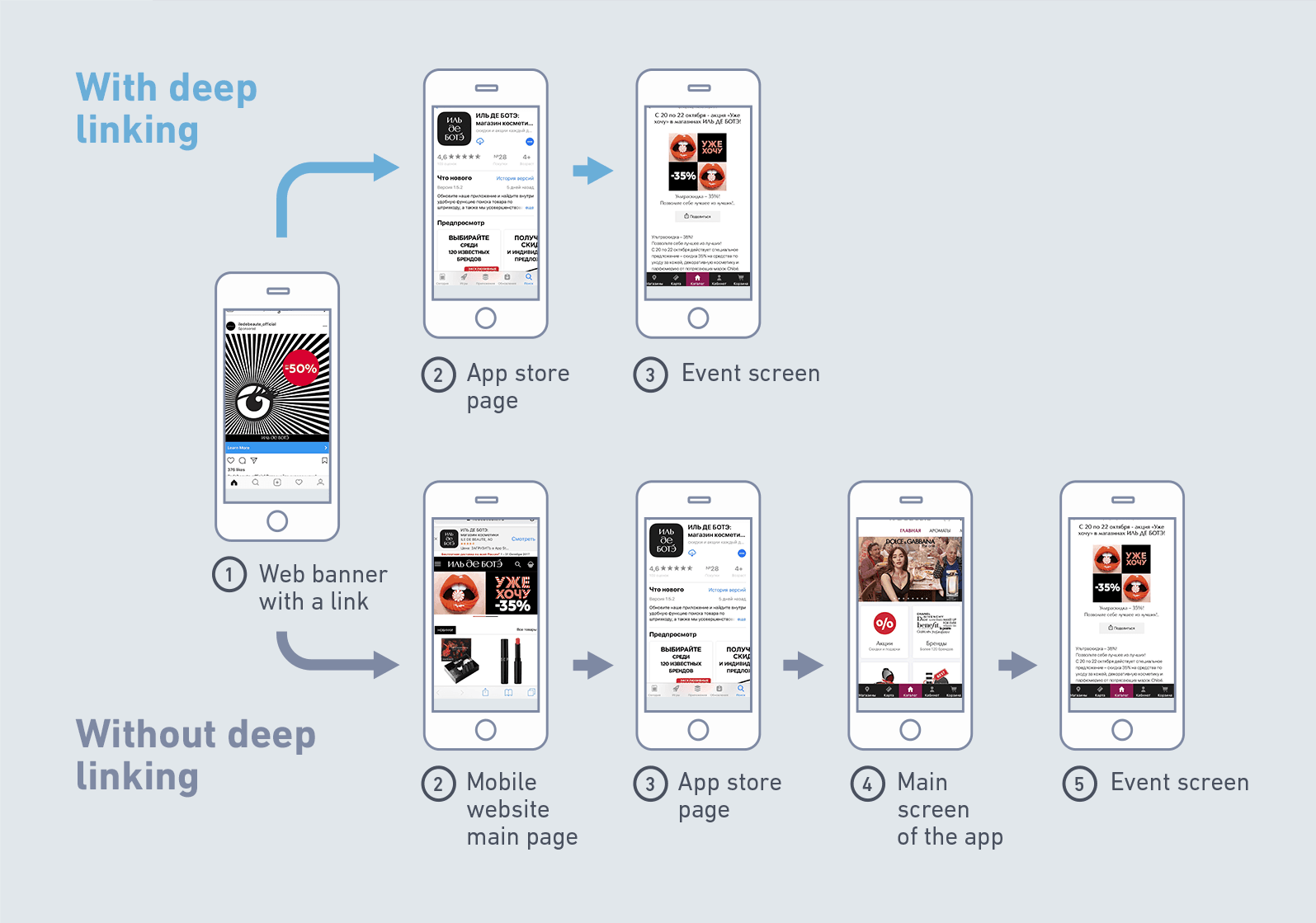
At the heart of this evolution lies the concept of the "deep hot link website," a term that is rapidly gaining traction. But what exactly is a deep hot link website? It's a question that demands careful consideration, as the answer has implications for how we access information, share content, and build online communities. To fully grasp its potential, we must first understand the building blocks that make it work, and the impact its already starting to have.
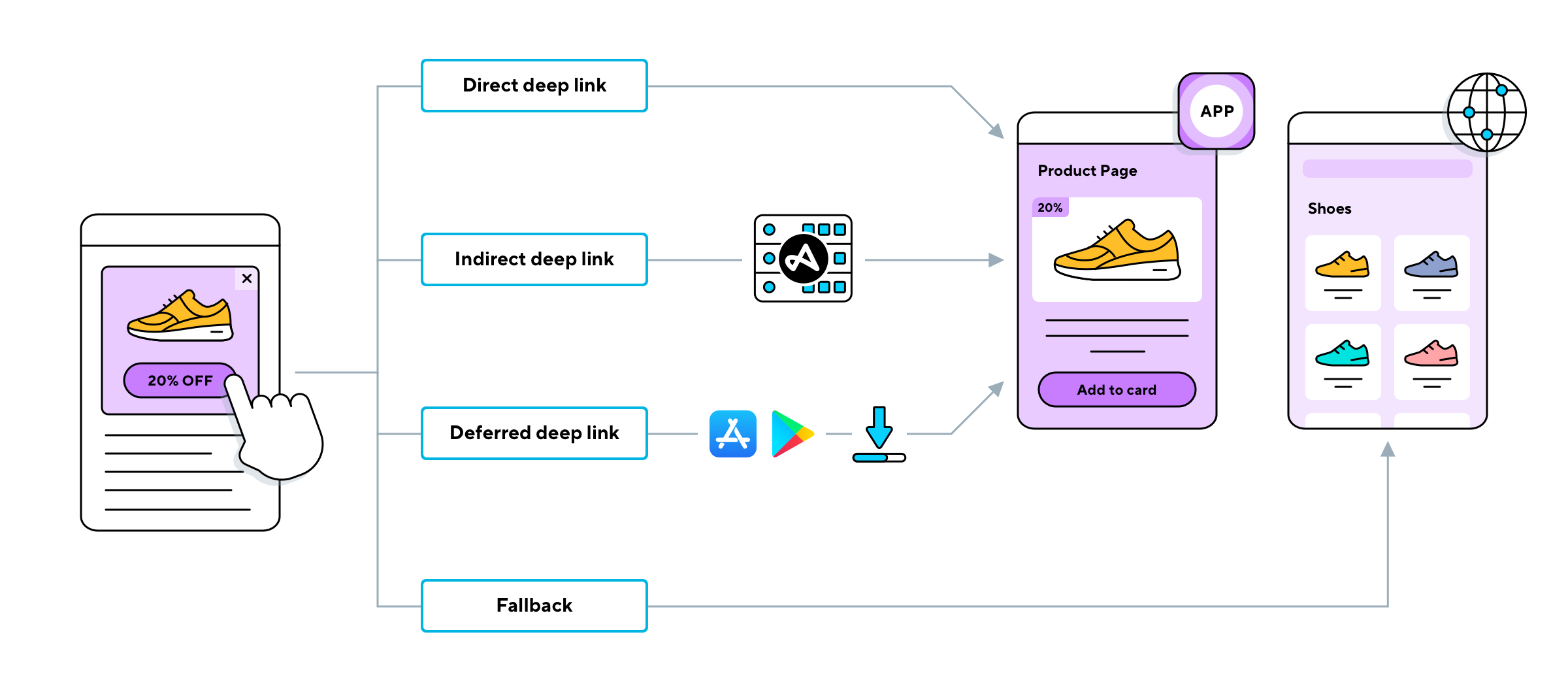
The mechanics of a deep hot link website are, at their core, quite simple. This link is made up of the authority and hostname, along with the instructions that dictate how it functions. The process of creating a deep link often begins with choosing a destinationthe specific page, content, or application the link will direct to. Once the destination is selected, the deep link URL needs to be generated. This is often achieved through specialized platforms or libraries, designed to create these unique URLs. These tools often include options for adding tracking or analytics parameters to monitor link performance. The final step involves embedding the deep link within the codebase, enabling seamless access and functionality.
This methodology can be incredibly useful for a variety of purposes. Consider the power of sharing links on social media platforms, simplifying complex URLs, and making the process more user-friendly. Imagine the efficiency of embedding links in email communications or printed materials, eliminating the need for clunky, lengthy web addresses. It's a strategy that promotes accessibility and streamlines the user experience, essential in today's fast-paced digital environment.
One striking area of application for such technologies revolves around the ever-evolving landscape of digital photography. The ability of "deephot.link" to enhance photography, by offering an immersive visual experience, is truly transformative. Imagine photographers unlocking new creative dimensions, showcasing their work with stunning detail and engaging viewers in ways that were previously unimaginable. This innovation also empowers photographers to better connect with their audiences.
The use of deep linking is not limited to photographic endeavors. It extends to various other facets of digital experiences, connecting to any computer at any time and offering smooth performance, even for gameplay, and often free for personal use! This accessibility can significantly expand the scope of what is possible.
However, the digital world also presents a complex duality. The rise of deepfakes, which are essentially manipulated videos and images, presents a serious challenge to our sense of reality and truth. The ease with which these AI-generated creations can be produced, and the increasing sophistication of the technology involved, is alarming. The line between genuine content and fabricated narratives is rapidly blurring, and the potential for misuse, ranging from misinformation campaigns to malicious content, is substantial. It is here that the term 'deepfakes porn videos' comes into play videos that appear real, of Bollywood personalities and others, often generated by AI, can deceive and mislead unsuspecting viewers.
In the shadowy corners of the internet, the generation of both pictures and videos is becoming increasingly prevalent. Although the origin often leans toward Indian content, the quality is remarkably high. Scenes are created that are so realistic that it becomes incredibly difficult to discern whether a scene is real or artificial, which poses very serious implications.
Amidst these digital shifts, the importance of data privacy cannot be overstated. The creation of solutions that combine ease of use with robust security features is paramount. In an era where the security of personal data is under constant scrutiny, technologies that prioritize privacy while still delivering functionality are crucial. Tools such as secure link management platforms become increasingly important to protect both creators and viewers from the potential harms of the digital landscape.
The following table provides a glimpse of the evolution of the concept of "deep hot link website" and its key components.
| Feature | Description | Implications |
|---|---|---|
| Deep Linking Technology | The core technology enabling the creation of deep links, which point directly to specific content or sections within a website or application. | Enhances user experience, facilitates content sharing, and streamlines navigation. |
| Link Management Platforms | Tools that help users create, manage, and track deep links, often including analytics and customization options. | Empowers users to control their links, measure their performance, and optimize content distribution. |
| Deepfake Integration | The use of deep linking to distribute and access deepfake content, including images and videos. | Raises ethical concerns, facilitates the spread of misinformation, and complicates the issue of digital authenticity. |
| Content Creation and Distribution | Utilizing deep links to share and access content such as images, videos, and other multimedia files. | Influences how content is consumed, distributed, and monetized, shifting the focus from traditional web browsing to targeted content. |
| Security and Privacy Measures | Protocols and tools designed to secure deep links and protect user data from misuse. | Enhances trust and user confidence in the digital environment, but requires vigilance to prevent abuse. |
The rise of technologies that seamlessly connect any computer to any time and provide smooth performance, even for gaming or personal use, highlights the evolution of digital access. This also encompasses the availability of content like Videos shruti hassan deep fake video 2, and similar content, is a part of this digital shift, but the potential of these technologies is far greater than their potential misuse.
The integration of advanced analytics, customizable options, and secure sharing capabilities in tools like deephot.link exemplifies this trend. It emphasizes the importance of user control, data privacy, and the ability to shape how content is shared and consumed. Consider the implications for businesses, marketers, and content creators, who can use these tools to understand user behavior, optimize campaigns, and personalize content delivery. This is a powerful tool, as long as it is used ethically.
The path ahead demands vigilance and a proactive approach. The rapid evolution of these technologies requires us to continuously evaluate their impact and ensure that we are building a digital landscape that promotes innovation, protects privacy, and fosters ethical behavior. The future depends on our ability to understand these complex forces and steer them toward a more positive, secure, and responsible digital future.