SSH IoT Access: Remote Access With IP Address Examples
Can you remotely and securely access your Internet of Things (IoT) devices, regardless of their location? The answer lies in the power of Secure Shell (SSH), a robust tool that provides a secure conduit for accessing and managing your devices from virtually anywhere in the world. This article dives deep into the intricacies of SSH and its application in the realm of IoT, offering practical examples and best practices to ensure your devices remain accessible and secure.
The landscape of IoT is rapidly expanding. From smart homes to intricate industrial automation systems, IoT devices have become ubiquitous. However, with this proliferation comes the critical need to secure these devices against unauthorized access and potential cyber threats. Traditional methods of remote access often fall short, particularly when dealing with devices that reside behind firewalls or utilize private IP addresses. This is where SSH shines, providing a secure and efficient means of overcoming these challenges.
To truly grasp the potential of SSH in the IoT domain, it's essential to understand its fundamental operation. SSH works by establishing a secure connection between a client program and an SSH server, often referred to as sshd. This connection ensures that all data transmitted is encrypted, safeguarding it from interception. In essence, SSH creates a secure tunnel, allowing you to securely manage your devices without exposing them to the vulnerabilities of the public internet.
Accessing IoT devices remotely using SSH requires a strategic approach, including obtaining the device's IP address, configuring the SSH server, and ensuring a secure connection. The following table outlines the key steps and considerations involved in setting up and utilizing SSH for your IoT devices:
| Step | Description | Key Considerations |
|---|---|---|
| Obtain the IoT Device's IP Address | The foundation of remote access is knowing the device's IP address. This is the unique identifier you'll use to connect. |
|
| Configure SSH on Your IoT Device | This involves installing and enabling the SSH server on your device. The specific steps will vary based on your device's operating system (e.g., Linux). |
|
| Configure Port Forwarding (if needed) | If your IoT device is behind a NAT (Network Address Translation) or firewall, you'll need to configure port forwarding on your router. |
|
| Obtain Your Public IP Address | To connect from outside your local network, you'll need your public IP address. |
|
| Connect via SSH from Anywhere | Once everything is set up, you can connect to your device from anywhere with an internet connection. |
|
Let's delve into the specifics. To begin, identifying the IP address of your IoT device is crucial. Several methods are available, depending on the device and its configuration. Some devices conveniently display their IP address on a connected screen or through an integrated interface. Another approach is to check your router's settings, where you can often find a list of connected devices and their corresponding IP addresses.
Understanding IP addresses is paramount in this process. Local IP addresses, frequently assigned in the 10.x.x.x or 192.168.x.x ranges, are used within your local network. However, IoT devices, by their nature, often do not have publicly reachable IP addresses. They are typically shielded behind firewalls, limiting direct access from the outside world. The gateway router plays a crucial role here, enabling the devices to communicate with the internet but also preventing direct external access.
Once you've identified the IP address, the next step involves setting up SSH on your IoT device. The specifics of this process depend on the operating system running on the device. For example, on many Linux-based systems, the SSH server (sshd) should start automatically. If it's not running, you might need to temporarily configure it. SSH works by connecting a client program to an SSH server, sshd. In many cases, the sshd server is already running on the remote_host that we specified. For security reasons, it is recommended to SSH your IoT device with the system user or SSH key-based secure authentication.
The core function of SSH is to provide a secure channel for accessing and controlling your devices from anywhere in the world. Using a command line or terminal window, you can establish a connection. This is typically achieved by using the ssh command, followed by the username and IP address of the device. For instance, the command ssh user@192.168.1.100 initiates a connection to the device with the IP address 192.168.1.100. If you are on a Linux machine, you can open a terminal window and enter the SSH command followed by the remote machine's IP address.
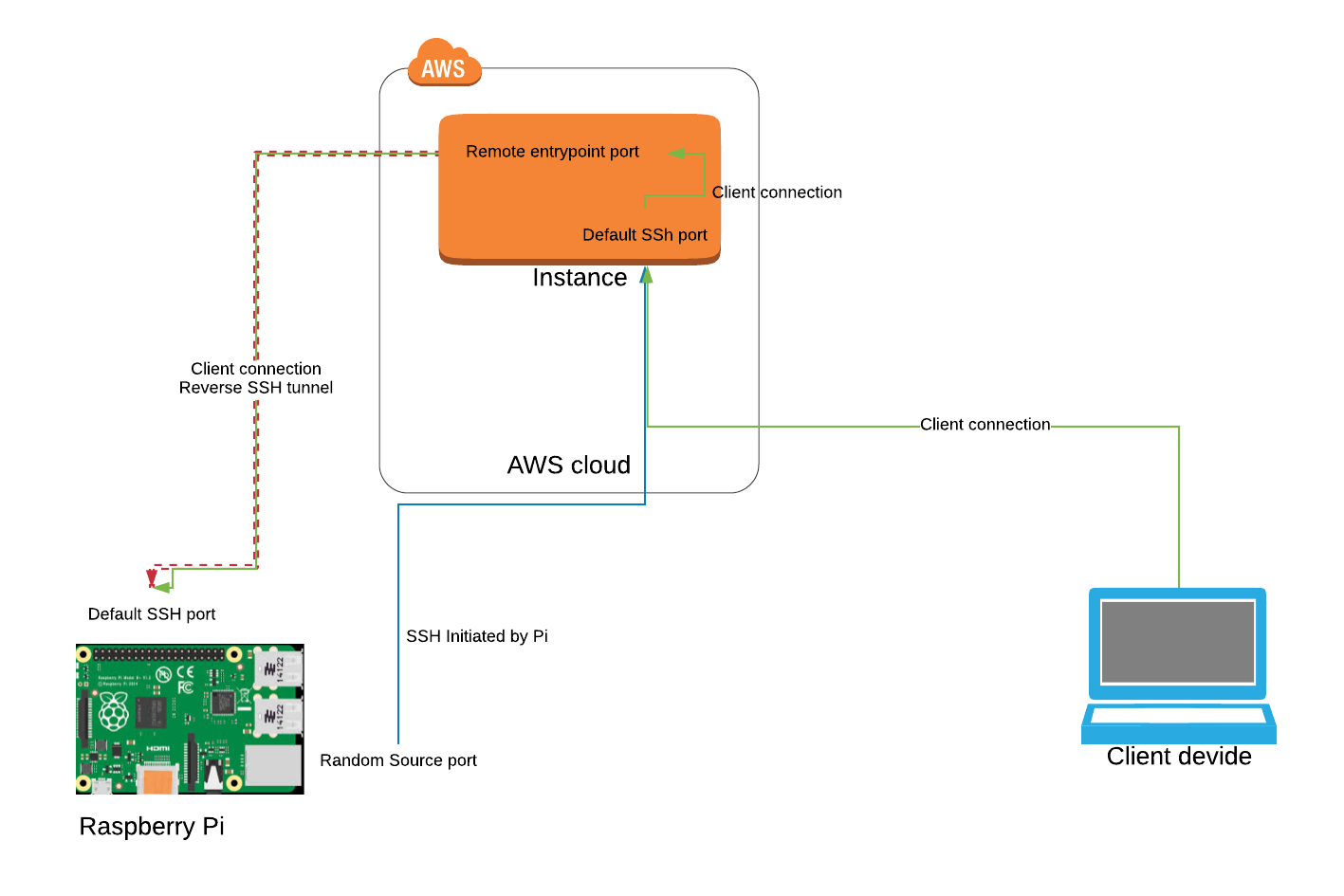
A crucial component in ensuring this remote access is the use of port forwarding on your router. If your IoT device is behind Network Address Translation (NAT), a firewall, or CGNAT, you will be unable to access it remotely without configuring port forwarding. The SSH server, by default, listens on TCP port 22. Youll need to configure your router to forward traffic on this port to the local IP address of your IoT device. This configuration effectively directs incoming connections to the intended device within your local network.
The power of SSH extends beyond mere remote access; it enables the secure management of your IoT devices. It allows you to monitor, configure, and troubleshoot your devices from anywhere with an internet connection. In today's world, where IoT devices are used in a variety of areas, from smart homes to industrial automation, the ability to securely manage these devices is essential for their proper functioning.
To reinforce the security aspect, always verify that your public IP address is correct. You can easily find your public IP address through various online resources. Furthermore, utilizing a static IP address for your IoT device can significantly simplify the connection process, ensuring that the server always has the same IP address, therefore establishing a stable remote connection.
Moreover, SSH is a powerful tool for managing your IoT devices remotely. By using SSH, you can manage your IoT devices from anywhere in the world, provided you have the correct IP address and credentials. The use of SSH provides a layer of security when managing your devices over the internet.
For increased security, consider using SSH key-based authentication. This involves generating a pair of keys a private key that you keep secret and a public key that you place on your IoT device. When you try to connect, the device verifies your identity by checking your private key against the public key. This method eliminates the need for passwords, making your connection more secure.
The process of accessing a remote server via SSH is streamlined. To connect, you'll need the server's IP address or its hostname. Once you have this information, open a terminal window on your local machine and enter the SSH command, followed by the remote machine's IP address. For example, ssh linuxconfig.org or ssh 10.1.1.1.
Managing IoT devices remotely often presents unique challenges, primarily ensuring the security of access. SSH addresses these challenges by establishing an encrypted tunnel for all communications, ensuring data privacy and security. Also, setting up DNS resolution on your server allows you to access your device using a domain name rather than an IP address, simplifying the connection process.
Remember that securing your IoT devices is an ongoing process, not a one-time setup. Regularly update the software and firmware on your devices to patch any security vulnerabilities. Also, implement strong passwords or, preferably, use SSH key-based authentication to protect your devices from unauthorized access. By embracing these security measures, you can confidently manage your IoT devices from anywhere in the world, reaping the benefits of remote access without compromising security.
In conclusion, SSH provides a secure, reliable, and versatile solution for accessing and managing your IoT devices remotely. By following the steps outlined in this guide, you can unlock the full potential of your IoT devices while maintaining a high level of security. With SSH, you have a powerful tool in your arsenal to navigate the increasingly interconnected world of IoT with confidence.
The following is a table that will help you with the technical details.
| Attribute | Details |
|---|---|
| Primary Function | Securely access and manage IoT devices remotely. |
| Mechanism | Uses SSH (Secure Shell) to establish encrypted connections. |
| Security Features | Data encryption, SSH key-based authentication, strong password practices. |
| Prerequisites | IoT device's IP address, SSH server configured on the device, port forwarding (if behind NAT). |
| Connection Method | Use the ssh [username]@[host_ip_address] command from a terminal. |
| Port | SSH server typically listens on TCP port 22 (can be customized). |
| Benefits | Secure access, remote management, troubleshooting, monitoring. |
| Considerations | Firewall and NAT configuration, public IP address verification, device software updates. |
| Applicability | Suitable for smart homes, industrial automation, and any application where remote IoT device management is required. |
| Advanced Techniques | Using a domain name instead of an IP address, implementing static IPs |
For more information, please visit SSH.com.