Secure SSH For IoT Devices On AWS: Your Ultimate Guide
Are you struggling to securely manage your Internet of Things (IoT) devices remotely? The key to unlocking secure and efficient IoT device management lies in mastering SSH (Secure Shell) on Amazon Web Services (AWS).
The world of IoT is expanding at an unprecedented rate. From smart agriculture to connected vehicles and industrial automation, the number of devices generating and transmitting data is exploding. Managing these devices, often deployed in remote locations or behind firewalls, presents significant challenges. Accessing these devices for troubleshooting, configuration updates, or security audits is crucial, but doing so securely is paramount. This is where Secure Shell (SSH) and AWS come into play, offering a robust solution for remote device management.
Let's delve into the core of this powerful combination, exploring the 'why' and the 'how' of implementing SSH for your IoT devices on AWS. This journey will cover the fundamentals, best practices, and essential tools needed to create a secure, efficient, and scalable IoT ecosystem.
So, what exactly makes access IoT SSH AWS such a powerful combination? The answer lies in the synergy between SSH's secure communication protocols and AWS's robust cloud infrastructure. AWS provides a comprehensive ecosystem for IoT deployments, including services like AWS IoT Core, which streamlines device connectivity and data processing. Integrating SSH into this framework enables you to remotely manage devices, troubleshoot issues, and perform secure updates. This capability is vital for several reasons, including:
- Security: SSH encrypts all communication between your device and the management server, protecting sensitive data from interception.
- Remote Access: SSH allows you to connect to devices located behind firewalls or in remote locations.
- Troubleshooting: SSH facilitates real-time diagnostics and issue resolution.
- Updates: SSH enables secure and efficient deployment of software updates.
Heres a deeper look into what makes this integration so crucial:
The Role of SSH in IoT Ecosystems
SSH is the backbone of secure remote access, and in the IoT context, it becomes indispensable. It allows authorized users to securely connect to and manage devices. This management extends to updating firmware, configuring settings, and diagnosing problems. Think of SSH as a secure tunnel that enables administrators to interact with their devices from anywhere in the world, provided they have the necessary permissions.
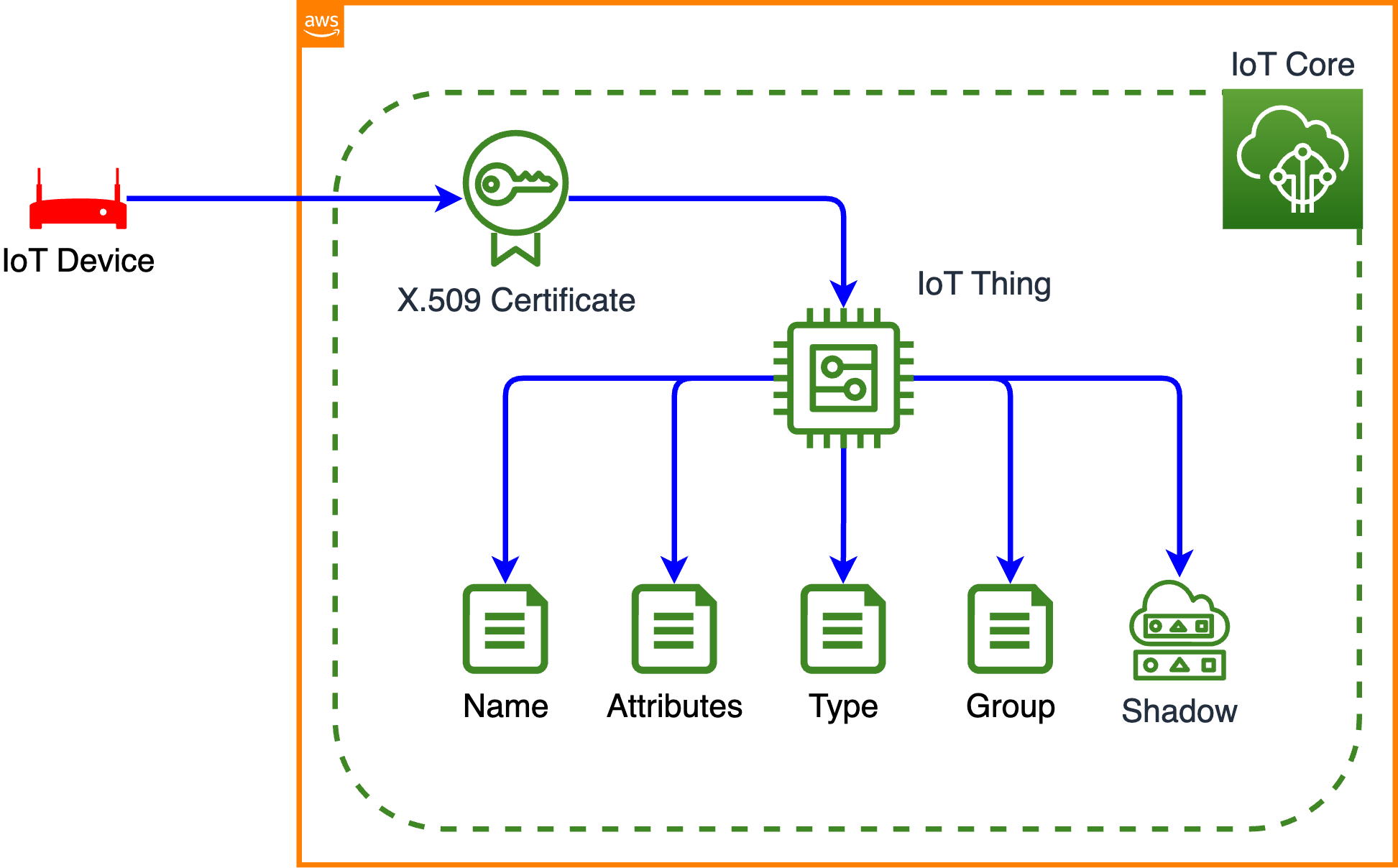
AWS IoT Core and the Cloud Advantage
AWS IoT Core acts as a central hub for all IoT devices. It facilitates device connectivity, data ingestion, and security. Using AWS IoT Core, you can efficiently manage and monitor your fleet of devices. In addition, AWS provides scalable, reliable, and secure infrastructure, making it an ideal environment for hosting your IoT applications. This combination offers a high degree of flexibility, reliability, and security, vital in the ever-changing landscape of IoT.
Real-World Applications Across Various Industries
The potential applications of remote SSH access to IoT devices on AWS are vast and span numerous industries. Consider these examples:
- Smart Agriculture: Farmers can remotely monitor and control irrigation systems, ensuring optimal water usage and crop health.
- Industrial Automation: Engineers can remotely manage and troubleshoot industrial machinery, reducing downtime and optimizing performance.
- Healthcare: Medical device technicians can securely access and maintain equipment, ensuring patient safety and operational efficiency.
- Smart Cities: City planners can remotely manage and maintain smart city infrastructure, such as traffic lights and environmental sensors.
Best Practices: A Key to Success
To achieve the best possible SSH to IoT device AWS setup, you need to adhere to best practices. These measures help optimize performance, enhance security, and reduce operational costs. Let's discuss some key recommendations:
- Use Public Key Authentication: Replace password-based logins with public key authentication for enhanced security. Public-key authentication uses a pair of keys (public and private) to verify user identity, significantly reducing the risk of unauthorized access.
- Disable Root Login: Disable root login to prevent unauthorized access. Grant specific permissions to the required users to perform administrative tasks.
- Regularly Update SSH Software: Keep your SSH software updated to patch security vulnerabilities.
- Implement Strong Security Policies: Set up robust firewall rules, monitor logs, and regularly review user access to maintain a high level of security.
Tools and Configurations for Secure Connections
Setting up an SSH connection to an IoT device over the internet using AWS and Windows might seem daunting at first, but with the right tools and knowledge, its entirely achievable. Here's what you need to know:
Prerequisites:
- An AWS account.
- An IoT device.
- A Windows machine.
- An SSH client (e.g., PuTTY, OpenSSH).
Step-by-Step Setup:
- Set up your Windows environment: Install an SSH client on your Windows machine. Configure it with the necessary parameters such as hostname/IP address, port, and user credentials.
- Configure AWS: Set up your AWS environment.
- Generate SSH Keys: Generate a public/private key pair on your Windows machine.
- Configure AWS IoT Core: Configure AWS IoT Core to manage the device.
- Establish the SSH Connection: Use the SSH client to connect to your IoT device.
The AWS IoT Managed Tunnel
AWS IoT Secure Tunneling is a managed service that simplifies establishing secure SSH connections. This feature allows you to open the SSH connection needed for your device, overcoming the challenges of devices behind restricted firewalls. The AWS IoT Secure Tunneling service provides a secure way to access remote devices, eliminating the need for you to manage public IP addresses, open ports, or deal with complex network configurations. It uses a reverse proxy approach, where a tunnel is established between the device and the AWS cloud. This service allows you to connect and troubleshoot devices remotely without compromising security.
For more information about using AWS IoT Secure Tunneling to connect to remote devices, see the "AWS IoT Secure Tunneling" section in the AWS IoT Developer Guide.
This approach not only enhances security but also simplifies the setup process, making it easier to remotely manage your IoT devices.
Optimizing Performance and Ensuring Compliance
Beyond the basics of setting up SSH, optimizing performance and ensuring compliance are essential aspects of managing SSH for IoT devices. Regular monitoring of network traffic, SSH server logs, and device performance metrics can help identify and resolve potential issues. Moreover, compliance with industry-specific regulations and best practices is necessary to ensure the safety and security of your IoT infrastructure. By taking these measures, you can maintain a secure, efficient, and compliant SSH setup for your IoT devices.
For instance, implementing regular security audits and vulnerability assessments can proactively identify and address potential threats, keeping your IoT devices safe.
A Comprehensive Guide to the Best SSH Practices
From understanding the basics of SSH to setting up your devices and following best practices, weve covered everything you need to know to keep your IoT ecosystem secure and efficient. Mastering SSH control of your IoT devices is your ultimate guide to secure connectivity.
Troubleshooting Common Issues
Even with a well-configured setup, you may encounter issues. Here are a few common problems and solutions:
- Connection Refused: Check your network connection, firewall settings, and SSH server configuration.
- Authentication Failed: Verify your username, password, and key pair.
- Slow Performance: Optimize your network connection, SSH configuration, and device resources.
Conclusion
As more organizations embrace cloud computing and IoT, finding the best remote SSH IoT device on AWS becomes crucial. Implementing best practices for IoT SSH AWS deployments can help organizations optimize performance, enhance security, and reduce operational costs. AWS provides a comprehensive suite of tools and services that enable secure and scalable IoT device management through SSH.